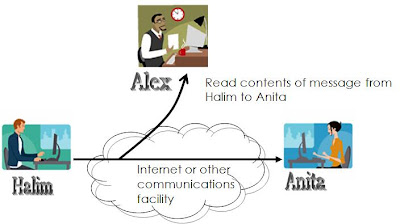
Passive Attacks: Traffic Analysis

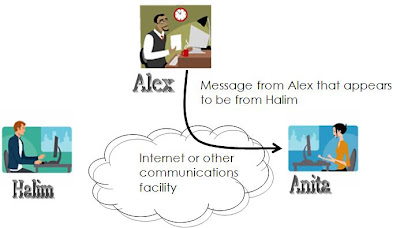
Active Attacks: Masquerade
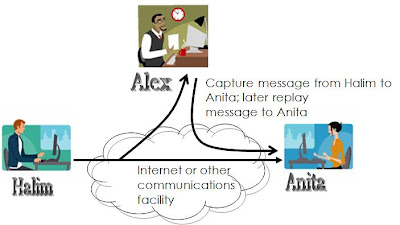
Active Attacks: Replay
Active Attacks: Modification of Messages

Active Attacks: Denial of Service

The introduction, general to advance informational blogs on IT Security and Security Equipment.


No comments:
Post a Comment