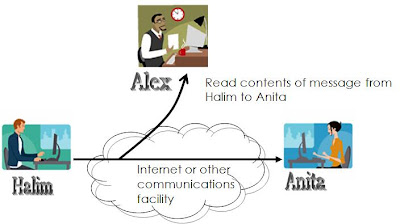
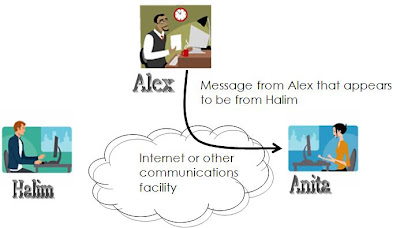
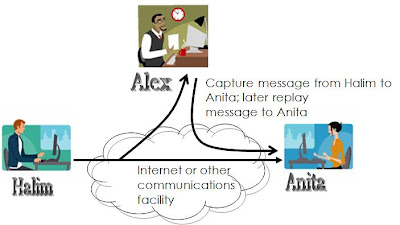
We can deal with harm that occurs when a threat is realized against a vulnerability in several ways:
- Prevent it, by blocking the attack or closing the vulnerability.
- Deter it, by making the attack harder, but not impossible.
- Deflect it, by making another target more attractive.
- Detect it, either as it happens or some time after the fact.
- Recover from its effects.
Controls:
- Encryption
- Software Controls - access limitations in a data base, in operating system protect each user from other users
- Hardware Controls –smartcard
- Policies - frequent changes of passwords
- Physical Controls
Software Controls:
- Program controls include:
- Internal program controls: part of the program that enforce security restrictions, such as access limitations in a database management program.
- Operating system and network system controls: limitations enforced by the operating system or network to protect each user from all other users.
- Independent control programs: application programs, such password checkers, intrusion detection utilities or virus scanners, that protect against certain types of vulnerabilities.
- Development controls: quality standards under which a program is designed, coded, tested and maintained, to prevent software faults from becoming exploitable vulnerabilities.
Hardware Controls:
- Numerous hardware devices have been created to assist in providing computer security. These devices include a variety of means, such as:
- Hardware or smart card implementations of encryption
- Locks or cables limiting access or deterring theft
- Devices to verify user’s identities
- Firewalls
- Intrusion detection systems
- Circuit boards that control access to storage media
Policies & Procedure Controls:
- Controls can also be in place based on agreed-upon procedures or policies among users, rather than enforcing security through hardware or software means.
- Training and administration follow immediately after establishment of policies, to reinforce the importance of security policy and to ensure their proper use.
Encryption Controls:
- Encryption is the formal name for scrambling data so that interpretation is meaningless without the intruder’s knowing how the scrambling was done.
- Encryption can virtually nullify the value of an interception and the possibility of effective modification or fabrication.
- It clearly addresses the need for confidentiality of data.
- It also can be used to ensure integrity.
- Encryption is the basis of protocols that enable us to provide security while accomplishing an important system or network task.
Effectiveness of Controls:
- Principle of effectiveness: Controls must be used and used properly to be effective.
- There are several aspects that can enhance the effectiveness of controls:
- Awareness of problem
- Likelihood of use
- Overlapping controls
- Periodic review