In cryptography, RSA (which stands for Rivest, Shamir, and Adleman who first publicly described it ; see below) is an algorithm for public-key cryptography. It is the first algorithm known to be suitable for signing as well as encryption, and one of the first great advances in public key cryptography. RSA is widely used in electronic commerce protocols, and is believed to be secure given sufficiently long keys and the use of up-to-date implementations.
Public key algorithm invented in 1977 by Ron Rivest, Adi Shamir and Leonard Adleman (RSA)
Supports Encryption and Digital Signatures
Most widely used public key algorithm
Gets its security from integer factorization problem
Relatively easy to understand and implement
Patent free (since 2000)
Operation
The RSA algorithm involves three steps: key generation, encryption and decryption.
RSA Usage
RSA is used in security protocols such as;
IPSEC/IKE - IP data security
TLS/SSL - transport data security (web)
PGP - email security
SSH - terminal connection security
SILC - conferencing service security
RSA Security
RSA gets its security from factorization problem. Difficulty of factoring large numbers is the basis of security of RSA. Over 1000 bits long numbers are used.
Integer factorization problem (finding number's prime factors):
Positive integer n, find its prime factors: n = p1 p2 ... pi where pi is positive distinct prime number
Example: 257603 = 41 * 61 * 103
Factorization algorithms can be used (attempted at least) to factor faster than brute forcing: Trial division, Pollard's rho, Pollard's p-1, Quadratic sieve, elliptic curve factorization, Random square factoring, Number field sieve, etc.
RSA Problem
RSA Problem (RSAP) is also the basis of security of RSA, in addition of factorization problem. The RSA problem assures the security of the RSA encryption and RSA digital signatures.
Implementation Tools
In order to implement RSA you will need:
Arbitrary precision arithmetic (multipleprecision arithmetic)
Pseudo Random Number Generator (PRNG)
Prime number generator
Difficulty of implementation greatly depends of the target platform, application usage and how much of the tools you need to implement from scratch.
Google search

Tuesday, September 1, 2009
Digital Signatures
Digital Signatures
A digital signature or digital signature scheme is a mathematical scheme for demonstrating the authenticity of a digital message or document. A valid digital signature gives a recipient reason to believe that the message was created by a known sender, and that it was not altered in transit. Digital signatures are commonly used for software distribution, financial transactions, and in other cases where it is important to detect forgery and tampering.
Uses of digital signatures
Authentication
Integrity
Some digital signature algorithms
Full Domain Hash, RSA-PSS etc., based on RSA
DSA
ECDSA
ElGamal signature scheme
Undeniable signature
SHA (typically SHA-1) with RSA
Rabin signature algorithm
Pointcheval-Stern signature algorithm
BLS
Schnorr signature
ECQV
Digital signature schemes share basic prerequisites that— regardless of cryptographic theory or legal provision— they need to have meaning:
1.Quality algorithms
Some public-key algorithms are known to be insecure, practicable attacks against them having been discovered.
2.Quality implementations
An implementation of a good algorithm (or protocol) with mistake(s) will not work.
3.The private key must remain private
if it becomes known to any other party, that party can produce perfect digital signatures of anything whatsoever.
4.The public key owner must be verifiable
A public key associated with Bob actually came from Bob. This is commonly done using a public key infrastructure and the public keyuser association is attested by the operator of the PKI (called a certificate authority). For 'open' PKIs in which anyone can request such an attestation (universally embodied in a cryptographically protected identity certificate), the possibility of mistaken attestation is non trivial. Commercial PKI operators have suffered several publicly known problems. Such mistakes could lead to falsely signed, and thus wrongly attributed, documents. 'closed' PKI systems are more expensive, but less easily subverted in this way.
5.Users (and their software) must carry out the signature protocol properly.
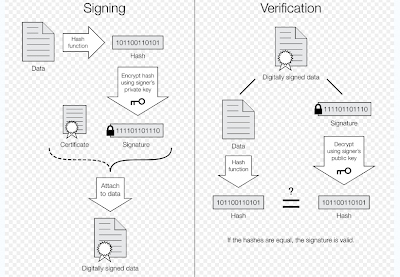
A digital signature or digital signature scheme is a mathematical scheme for demonstrating the authenticity of a digital message or document. A valid digital signature gives a recipient reason to believe that the message was created by a known sender, and that it was not altered in transit. Digital signatures are commonly used for software distribution, financial transactions, and in other cases where it is important to detect forgery and tampering.
Uses of digital signatures
Authentication
Integrity
Some digital signature algorithms
Full Domain Hash, RSA-PSS etc., based on RSA
DSA
ECDSA
ElGamal signature scheme
Undeniable signature
SHA (typically SHA-1) with RSA
Rabin signature algorithm
Pointcheval-Stern signature algorithm
BLS
Schnorr signature
ECQV
Digital signature schemes share basic prerequisites that— regardless of cryptographic theory or legal provision— they need to have meaning:
1.Quality algorithms
Some public-key algorithms are known to be insecure, practicable attacks against them having been discovered.
2.Quality implementations
An implementation of a good algorithm (or protocol) with mistake(s) will not work.
3.The private key must remain private
if it becomes known to any other party, that party can produce perfect digital signatures of anything whatsoever.
4.The public key owner must be verifiable
A public key associated with Bob actually came from Bob. This is commonly done using a public key infrastructure and the public keyuser association is attested by the operator of the PKI (called a certificate authority). For 'open' PKIs in which anyone can request such an attestation (universally embodied in a cryptographically protected identity certificate), the possibility of mistaken attestation is non trivial. Commercial PKI operators have suffered several publicly known problems. Such mistakes could lead to falsely signed, and thus wrongly attributed, documents. 'closed' PKI systems are more expensive, but less easily subverted in this way.
5.Users (and their software) must carry out the signature protocol properly.

Data Availibility
Data Availibility.
Although it is important that data remains secure and confidential, it
is just as important that the data is available when needed. Secured
data that is inaccessible is considered downtime and detrimental to
a business and its ability to serve customers. Technologies such
as clustering and load balancing can help, but if NTFS permissions
are assigned inappropriately, these features will not help.
Log on to the Windows 2003 server as Administrator.
1. Open My Computer and then double-click on the D drive.
2. Create a new folder called Availability.
3. Double-click the Availability folder and create the folder User2Folder.
4. Right-click on User2Folder.
5. Follow step 6 to 20 in the previous task to secure the folder so that only User2 can access it.
6. Log on as User2 and verify that you have access to d:\Availability\User2Folder.
7. Close all windows and log off.
8. Log on as Administrator and delete the User2 account from the local security database.
9. Create a new user, also named User2, then log off.
10. Logon as User2 and try to access the d:\Availability\User2Folder. Access should be denied.
11. Log off User2.
12. Log on as Administrator.
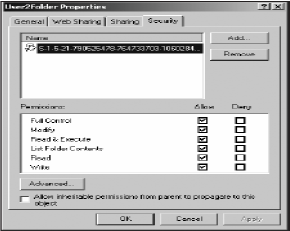
13. Check the Security properties of the d:\Availability\User2Folder. Notice the account is no longer listed, but the old SID is. Your properties should look
like those below.
14. You should be denied access. The data is no longeravailable to User2.
15. To verify this, log on as User2 and try to open the User2Folder.You will be denied access.
16. Close all windows and log off.

Although it is important that data remains secure and confidential, it
is just as important that the data is available when needed. Secured
data that is inaccessible is considered downtime and detrimental to
a business and its ability to serve customers. Technologies such
as clustering and load balancing can help, but if NTFS permissions
are assigned inappropriately, these features will not help.
Log on to the Windows 2003 server as Administrator.
1. Open My Computer and then double-click on the D drive.
2. Create a new folder called Availability.
3. Double-click the Availability folder and create the folder User2Folder.
4. Right-click on User2Folder.
5. Follow step 6 to 20 in the previous task to secure the folder so that only User2 can access it.
6. Log on as User2 and verify that you have access to d:\Availability\User2Folder.
7. Close all windows and log off.
8. Log on as Administrator and delete the User2 account from the local security database.
9. Create a new user, also named User2, then log off.
10. Logon as User2 and try to access the d:\Availability\User2Folder. Access should be denied.
11. Log off User2.
12. Log on as Administrator.
13. Check the Security properties of the d:\Availability\User2Folder. Notice the account is no longer listed, but the old SID is. Your properties should look
like those below.

14. You should be denied access. The data is no longeravailable to User2.
15. To verify this, log on as User2 and try to open the User2Folder.You will be denied access.
16. Close all windows and log off.

Data Confidentiality (NTFS permissions)
Data Confidentiality (NTFS permissions)
Use NTFS permissions to specify which users and groups can gain access to files and folders, and what they can do with the contents of the file or folder. NTFS permissions are only available on NTFS volumes. The permissions you assign for folders are different from the permissions you assign for files.
You assign folder permissions to control the access that users have to folders and to the files and subfolders that are contained within the folder.

Creating user account
1. Two user-level accounts: User1 and User2
a. To create user account go to [Start] | [Administrative Tools] | [Computer Management].
b. Choose [Local User and Groups] and double click on the [user] folder.
c. To create new user right click on the pane and from the pop-up menu choose [New User] and fill up the necessary information such as username and password (use easy to remember password e.g. abc123)


Creating data Confidentiality between 2 user accounts.
1. Log on to the Windows 2003 server as Administrator.
2. Open My Computer, and then double-click on the D: drive. This should be the drive that was converted from FAT to NTFS in task 1
3. Create a new folder called Confidentiality.
4. Double-click the Confidentiality folder and create a new folder called User1Folder.
5. To secure this folder from other users, right-click User1Folder.
6. Click [Properties] to open the User1Folder Properties window.
7. Click the [Security] tab, as seen in Figure 2.3. Note: if the drive was not formatted with NTFS the Security tab will be unavailable
.JPG)
Click on the Advanced Button, you will receive a windows as
shown in figure below
.JPG)
Uncheck the box “Allow inheritable permissions from parent to propagate to this object”.
10. You will receive the message shown in figure below
.JPG)
11. Click [Copy] to retain the permissions.
12. Click [Add] and the Select Users, Computers, or Groups window will pop up.
13. Type User1 and then click [Checks Names].

14. Click [OK].
15. In the Permission Entry windows, click the Allow Full Control box and then click [OK].
16. Remove the other username except Administrator, System
and User1 by clicking the username and click the [Remove] button.

17. Click OK.
18. Double-click User1Folder.and you should see the content of the folder
19. Close all windows and log off.
20. Log on as User2 and navigate to the User1Folder, can you open it?
21. Close all windows and log off.
Use NTFS permissions to specify which users and groups can gain access to files and folders, and what they can do with the contents of the file or folder. NTFS permissions are only available on NTFS volumes. The permissions you assign for folders are different from the permissions you assign for files.
You assign folder permissions to control the access that users have to folders and to the files and subfolders that are contained within the folder.

Creating user account
1. Two user-level accounts: User1 and User2
a. To create user account go to [Start] | [Administrative Tools] | [Computer Management].
b. Choose [Local User and Groups] and double click on the [user] folder.
c. To create new user right click on the pane and from the pop-up menu choose [New User] and fill up the necessary information such as username and password (use easy to remember password e.g. abc123)


Creating data Confidentiality between 2 user accounts.
1. Log on to the Windows 2003 server as Administrator.
2. Open My Computer, and then double-click on the D: drive. This should be the drive that was converted from FAT to NTFS in task 1
3. Create a new folder called Confidentiality.
4. Double-click the Confidentiality folder and create a new folder called User1Folder.
5. To secure this folder from other users, right-click User1Folder.
6. Click [Properties] to open the User1Folder Properties window.
7. Click the [Security] tab, as seen in Figure 2.3. Note: if the drive was not formatted with NTFS the Security tab will be unavailable
.JPG)
Click on the Advanced Button, you will receive a windows as
shown in figure below
.JPG)
Uncheck the box “Allow inheritable permissions from parent to propagate to this object”.
10. You will receive the message shown in figure below
.JPG)
11. Click [Copy] to retain the permissions.
12. Click [Add] and the Select Users, Computers, or Groups window will pop up.
13. Type User1 and then click [Checks Names].

14. Click [OK].
15. In the Permission Entry windows, click the Allow Full Control box and then click [OK].
16. Remove the other username except Administrator, System
and User1 by clicking the username and click the [Remove] button.

17. Click OK.
18. Double-click User1Folder.and you should see the content of the folder
19. Close all windows and log off.
20. Log on as User2 and navigate to the User1Folder, can you open it?
21. Close all windows and log off.
Subscribe to:
Posts (Atom)

