A digital signature or digital signature scheme is a mathematical scheme for demonstrating the authenticity of a digital message or document. A valid digital signature gives a recipient reason to believe that the message was created by a known sender, and that it was not altered in transit. Digital signatures are commonly used for software distribution, financial transactions, and in other cases where it is important to detect forgery and tampering.
Uses of digital signatures
Authentication
Integrity
Some digital signature algorithms
Full Domain Hash, RSA-PSS etc., based on RSA
DSA
ECDSA
ElGamal signature scheme
Undeniable signature
SHA (typically SHA-1) with RSA
Rabin signature algorithm
Pointcheval-Stern signature algorithm
BLS
Schnorr signature
ECQV
Digital signature schemes share basic prerequisites that— regardless of cryptographic theory or legal provision— they need to have meaning:
1.Quality algorithms
Some public-key algorithms are known to be insecure, practicable attacks against them having been discovered.
2.Quality implementations
An implementation of a good algorithm (or protocol) with mistake(s) will not work.
3.The private key must remain private
if it becomes known to any other party, that party can produce perfect digital signatures of anything whatsoever.
4.The public key owner must be verifiable
A public key associated with Bob actually came from Bob. This is commonly done using a public key infrastructure and the public keyuser association is attested by the operator of the PKI (called a certificate authority). For 'open' PKIs in which anyone can request such an attestation (universally embodied in a cryptographically protected identity certificate), the possibility of mistaken attestation is non trivial. Commercial PKI operators have suffered several publicly known problems. Such mistakes could lead to falsely signed, and thus wrongly attributed, documents. 'closed' PKI systems are more expensive, but less easily subverted in this way.
5.Users (and their software) must carry out the signature protocol properly.



nice
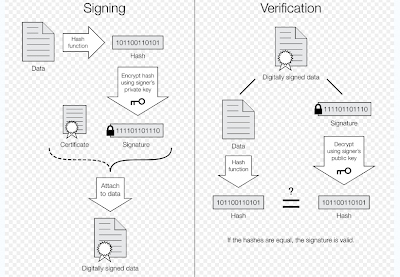
ReplyDeleteAppreciating. You have described the entire concept and how digital signature works in a very pleasing way. The above figure portrays the complete working and one can easily understand how all the things are working. Thanks.
ReplyDeletee-sign act